Alibaba Cloud Integration
RustFS provides seamless integration with Alibaba Cloud services, enabling hybrid and multi-cloud storage solutions with optimal performance and cost efficiency.
Overview
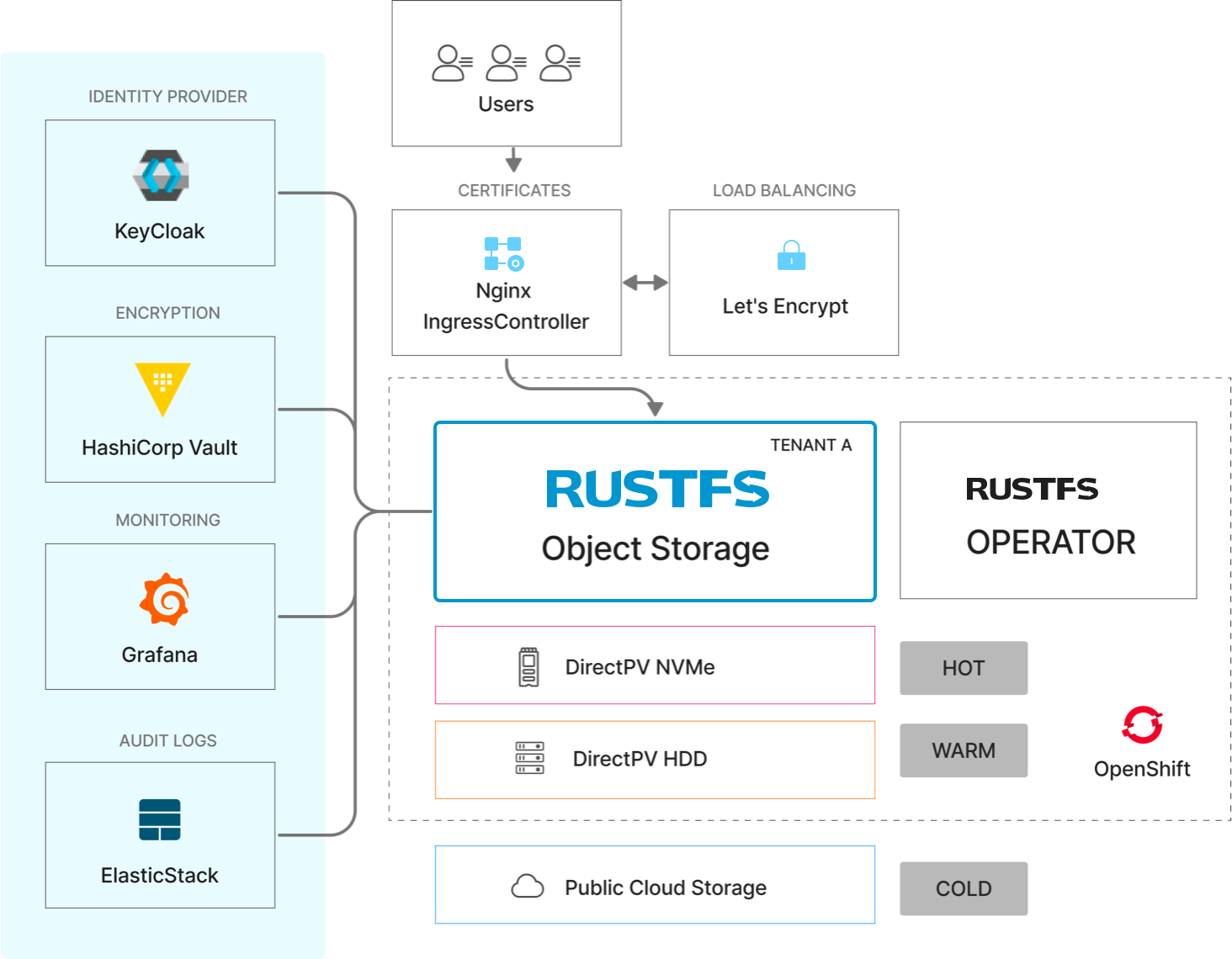
RustFS on Alibaba Cloud offers:
- Native Integration: Deep integration with Alibaba Cloud services
- Hybrid Architecture: Seamless connection between on-premises and cloud
- Cost Optimization: Intelligent tiering and lifecycle management
- High Performance: Optimized for Alibaba Cloud infrastructure
Key Features
Seamless Cloud Integration
- ECS Integration: Deploy on Elastic Compute Service instances
- OSS Compatibility: Compatible with Object Storage Service APIs
- VPC Support: Deploy within Virtual Private Cloud for security
- CDN Integration: Accelerate content delivery with Alibaba Cloud CDN
Storage Optimization
- Intelligent Tiering: Automatic data movement between storage tiers
- Lifecycle Management: Automated data lifecycle policies
- Compression: Built-in data compression to reduce storage costs
- Deduplication: Eliminate duplicate data to optimize storage
Security and Compliance
- Encryption: End-to-end encryption with KMS integration
- Access Control: Fine-grained access control and IAM integration
- Audit Logging: Comprehensive audit trails and compliance reporting
- Network Security: VPC, security groups, and network ACLs
Deployment Architectures
Hybrid Cloud Architecture
┌─────────────────┐ ┌─────────────────┐
│ On-Premises │ │ Alibaba Cloud │
│ RustFS │◄──►│ RustFS │
│ │ │ │
│ • Primary Data │ │ • Backup Data │
│ • Hot Storage │ │ • Cold Storage │
│ • Low Latency │ │ • Cost Optimized│
└─────────────────┘ └─────────────────┘Multi-Region Deployment
┌─────────────────┐ ┌─────────────────┐
│ Region A │ │ Region B │
│ (Primary) │◄──►│ (Backup) │
│ │ │ │
│ • Active Data │ │ • Replica Data │
│ • Read/Write │ │ • Read Only │
│ • Low Latency │ │ • DR Ready │
└─────────────────┘ └─────────────────┘Integration Services
Compute Services
Elastic Compute Service (ECS)
- Optimized Instances: Recommended instance types for RustFS
- Auto Scaling: Automatic scaling based on workload
- Load Balancing: Distribute traffic across multiple instances
- Health Monitoring: Continuous health checks and alerting
Container Services
- ACK Integration: Deploy on Alibaba Cloud Container Service for Kubernetes
- Serverless Kubernetes: Serverless container deployment
- Service Mesh: Integration with Alibaba Service Mesh
- DevOps: CI/CD pipeline integration
Storage Services
Object Storage Service (OSS)
- API Compatibility: S3-compatible API for seamless migration
- Tiering: Automatic tiering to OSS IA and Archive
- Cross-Region Replication: Replicate data across regions
- Lifecycle Policies: Automated data lifecycle management
Network Attached Storage (NAS)
- File System Interface: POSIX-compliant file system access
- Performance Tiers: General Purpose and Performance tiers
- Backup Integration: Automated backup to OSS
- Access Control: Fine-grained file-level permissions
Network Services
Virtual Private Cloud (VPC)
- Isolated Network: Deploy in isolated network environment
- Subnets: Organize resources across multiple subnets
- Route Tables: Custom routing for optimal performance
- NAT Gateway: Secure internet access for private instances
Content Delivery Network (CDN)
- Global Acceleration: Accelerate content delivery worldwide
- Cache Optimization: Intelligent caching strategies
- HTTPS Support: Secure content delivery with SSL/TLS
- Real-time Analytics: Monitor CDN performance and usage
Security Integration
Key Management Service (KMS)
- Encryption Keys: Centralized encryption key management
- Hardware Security Modules: HSM-backed key protection
- Key Rotation: Automatic key rotation policies
- Audit Logging: Complete key usage audit trails
Identity and Access Management (IAM)
- User Management: Centralized user and role management
- Policy-Based Access: Fine-grained access control policies
- Multi-Factor Authentication: Enhanced security with MFA
- Federation: Integration with external identity providers
Security Center
- Threat Detection: Real-time threat detection and response
- Vulnerability Assessment: Regular security assessments
- Compliance Monitoring: Continuous compliance monitoring
- Incident Response: Automated incident response workflows
Monitoring and Operations
CloudMonitor
- Performance Metrics: Monitor storage performance and usage
- Custom Dashboards: Create custom monitoring dashboards
- Alerting: Set up alerts for critical metrics
- Log Analysis: Analyze system and application logs
Log Service
- Centralized Logging: Collect and analyze all system logs
- Real-time Analysis: Real-time log processing and analysis
- Search and Query: Powerful search and query capabilities
- Integration: Integration with monitoring and alerting systems
Cost Optimization
Pricing Models
- Pay-as-you-go: Pay only for resources used
- Subscription: Reserved capacity for predictable workloads
- Spot Instances: Use spot instances for cost savings
- Resource Packages: Bundled resources for better pricing
Cost Management
- Usage Monitoring: Monitor resource usage and costs
- Budget Alerts: Set up budget alerts and notifications
- Cost Analysis: Detailed cost analysis and optimization recommendations
- Reserved Instances: Purchase reserved instances for cost savings
Best Practices
Performance Optimization
- Instance Selection: Choose appropriate instance types for workload
- Network Optimization: Use enhanced networking for better performance
- Storage Configuration: Optimize storage configuration for performance
- Caching: Implement caching strategies for frequently accessed data
Security Best Practices
- Network Security: Use VPC and security groups for network isolation
- Encryption: Enable encryption for data at rest and in transit
- Access Control: Implement least privilege access control
- Monitoring: Continuous security monitoring and alerting
Cost Optimization
- Right-sizing: Regularly review and optimize instance sizes
- Storage Tiering: Use appropriate storage tiers for different data types
- Reserved Capacity: Purchase reserved instances for predictable workloads
- Lifecycle Policies: Implement automated data lifecycle policies
Migration Services
Assessment and Planning
- Current State Analysis: Assess existing infrastructure and workloads
- Migration Strategy: Develop comprehensive migration strategy
- Risk Assessment: Identify and mitigate migration risks
- Timeline Planning: Create detailed migration timeline
Data Migration
- Migration Tools: Use Alibaba Cloud migration tools and services
- Data Transfer: High-speed data transfer services
- Validation: Data integrity validation and verification
- Rollback: Safe rollback procedures if needed
Application Migration
- Application Assessment: Assess application compatibility
- Refactoring: Refactor applications for cloud optimization
- Testing: Comprehensive testing in cloud environment
- Go-live: Coordinated go-live and cutover procedures
Support and Services
Technical Support
- 24/7 Support: Round-the-clock technical support
- Dedicated Support: Dedicated support for enterprise customers
- Expert Consultation: Access to cloud architecture experts
- Training: Comprehensive training programs
Professional Services
- Architecture Design: Design optimal cloud architecture
- Implementation: Professional implementation services
- Migration: End-to-end migration services
- Optimization: Ongoing optimization and tuning services
Getting Started
Prerequisites
- Alibaba Cloud Account: Set up Alibaba Cloud account
- VPC Setup: Configure Virtual Private Cloud
- Security Configuration: Set up security groups and access controls
- Network Configuration: Configure network connectivity
Quick Start
- Launch ECS Instances: Launch compute instances for RustFS
- Install RustFS: Install and configure RustFS software
- Configure Storage: Set up storage volumes and configuration
- Test Connectivity: Verify connectivity and performance
- Production Deployment: Deploy to production environment
Next Steps
- Monitoring Setup: Configure monitoring and alerting
- Backup Configuration: Set up backup and disaster recovery
- Performance Tuning: Optimize performance for workloads
- Security Hardening: Implement additional security measures