Huawei Cloud Integration
RustFS provides comprehensive integration with Huawei Cloud services, enabling secure, compliant, and high-performance storage solutions for enterprise customers.
Overview
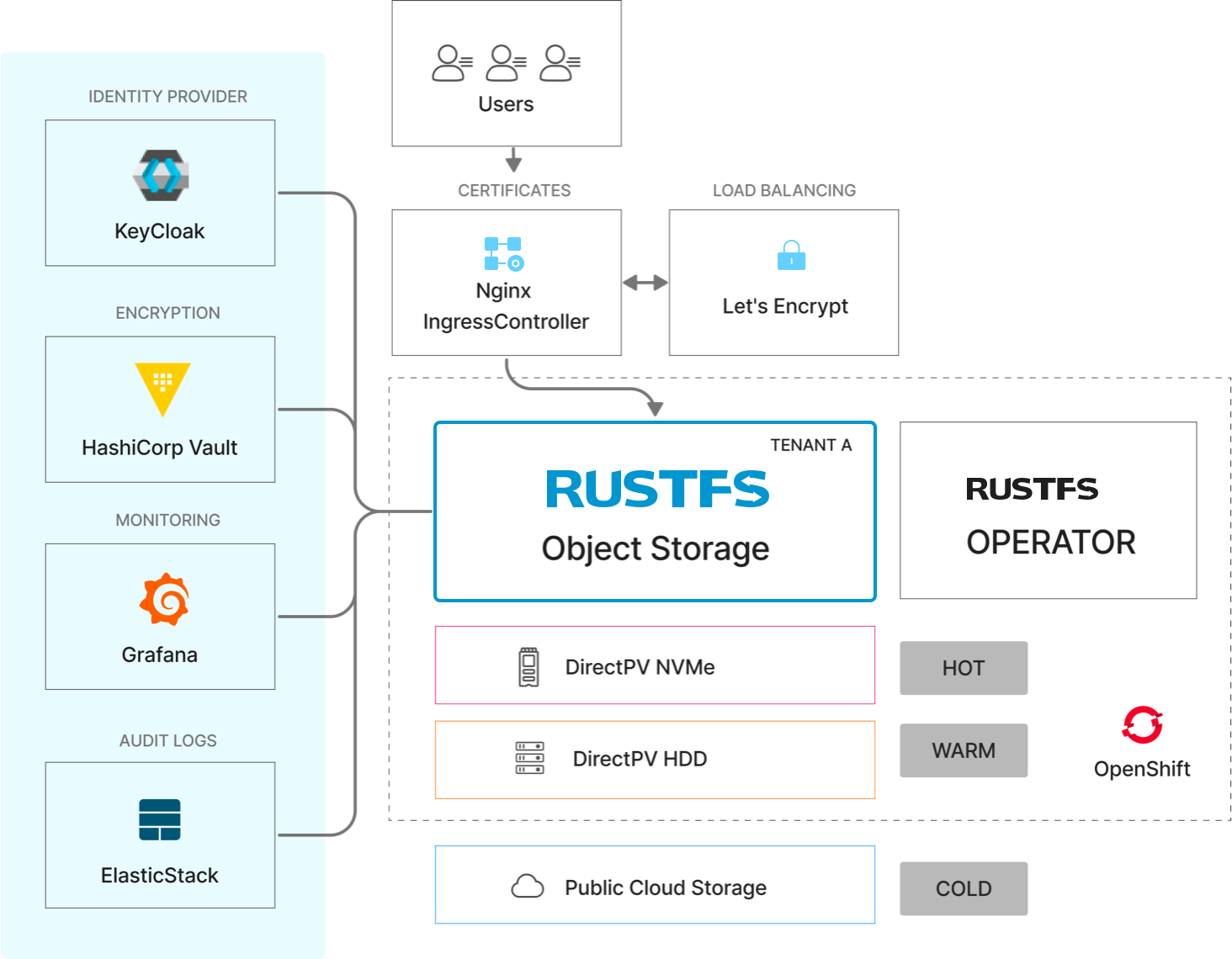
RustFS on Huawei Cloud delivers:
- Native Integration: Deep integration with Huawei Cloud services
- Enterprise Security: Enhanced security and compliance features
- High Performance: Optimized for Huawei Cloud infrastructure
- Cost Efficiency: Intelligent resource management and optimization
Core Integrations
Compute Services
Elastic Cloud Server (ECS)
- Optimized Instances: Recommended instance types for storage workloads
- Auto Scaling: Automatic scaling based on demand
- High Availability: Multi-AZ deployment for fault tolerance
- Performance Optimization: CPU and memory optimization for storage
Cloud Container Engine (CCE)
- Kubernetes Deployment: Deploy RustFS on managed Kubernetes
- Container Storage: Integration with cloud storage services
- Service Mesh: Integration with Istio service mesh
- DevOps Pipeline: CI/CD integration with CodeArts
Storage Services
Object Storage Service (OBS)
- S3 Compatibility: Full S3 API compatibility
- Intelligent Tiering: Automatic data tiering to optimize costs
- Cross-Region Replication: Multi-region data replication
- Lifecycle Management: Automated data lifecycle policies
Elastic Volume Service (EVS)
- High-Performance Storage: SSD and Ultra-high I/O volumes
- Snapshot Management: Automated backup and snapshot management
- Encryption: Built-in encryption with KMS integration
- Multi-Attach: Shared storage across multiple instances
Scalable File Service (SFS)
- NFS Protocol: POSIX-compliant file system interface
- Performance Tiers: Standard and Performance file systems
- Capacity Scaling: Automatic capacity scaling
- Access Control: Fine-grained access control
Network Services
Virtual Private Cloud (VPC)
- Network Isolation: Secure isolated network environment
- Subnets: Multi-AZ subnet deployment
- Security Groups: Fine-grained network access control
- VPC Peering: Cross-VPC connectivity
Elastic Load Balance (ELB)
- Traffic Distribution: Distribute traffic across multiple instances
- Health Checks: Automatic health monitoring
- SSL Termination: SSL/TLS termination at load balancer
- Session Persistence: Session affinity support
Content Delivery Network (CDN)
- Global Acceleration: Accelerate content delivery worldwide
- Edge Caching: Intelligent edge caching strategies
- HTTPS Support: Secure content delivery
- Real-time Monitoring: Performance and usage analytics
Security Integration
Identity and Access Management (IAM)
- Fine-grained Permissions: Precise access control policies
- Role-based Access: IAM roles and policies
- Multi-Factor Authentication: Enhanced security with MFA
- Federation: Integration with enterprise identity systems
Key Management Service (KMS)
- Encryption Key Management: Centralized key management
- Hardware Security Modules: HSM-backed key protection
- Key Rotation: Automatic key rotation policies
- Compliance: Meet regulatory compliance requirements
Cloud Trace Service (CTS)
- API Auditing: Complete audit trail of all operations
- Compliance Reporting: Automated compliance reporting
- Security Analysis: Security event analysis and monitoring
- Integration: Integration with SIEM systems
Web Application Firewall (WAF)
- Application Protection: Protect against web attacks
- DDoS Protection: Distributed denial of service protection
- Bot Management: Automated bot detection and mitigation
- Custom Rules: Custom security rules and policies
Monitoring and Operations
Cloud Eye
- Performance Monitoring: Monitor system and application metrics
- Custom Metrics: Create custom monitoring metrics
- Alerting: Set up alerts and notifications
- Dashboards: Custom monitoring dashboards
Log Tank Service (LTS)
- Centralized Logging: Collect and analyze all system logs
- Real-time Analysis: Real-time log processing
- Search and Query: Powerful log search capabilities
- Integration: Integration with monitoring systems
Application Performance Management (APM)
- Performance Monitoring: Monitor application performance
- Distributed Tracing: Trace requests across services
- Error Analysis: Identify and analyze errors
- Performance Optimization: Performance tuning recommendations
Deployment Architectures
Single-Region Deployment
┌─────────────────┐
│ Huawei Cloud │
│ Region │
│ │
│ ┌─────────────┐│
│ │ AZ-1 ││
│ │ RustFS ││
│ │ Node 1-2 ││
│ └─────────────┘│
│ │
│ ┌─────────────┐│
│ │ AZ-2 ││
│ │ RustFS ││
│ │ Node 3-4 ││
│ └─────────────┘│
└─────────────────┘Multi-Region Deployment
┌─────────────────┐ ┌─────────────────┐
│ Primary │ │ Secondary │
│ Region │◄──►│ Region │
│ │ │ │
│ • Active Data │ │ • Replica Data │
│ • Read/Write │ │ • Read Only │
│ • Low Latency │ │ • DR Ready │
└─────────────────┘ └─────────────────┘Hybrid Cloud Architecture
┌─────────────────┐ ┌─────────────────┐
│ On-Premises │ │ Huawei Cloud │
│ RustFS │◄──►│ RustFS │
│ │ │ │
│ • Primary Data │ │ • Backup Data │
│ • Hot Storage │ │ • Cold Storage │
│ • Low Latency │ │ • Cost Optimized│
└─────────────────┘ └─────────────────┘Industry Solutions
Government and Public Sector
- Compliance: Meet government security and compliance requirements
- Data Sovereignty: Ensure data remains within national boundaries
- Security Clearance: Support for classified data handling
- Audit Trail: Complete audit trails for regulatory compliance
Financial Services
- Regulatory Compliance: Meet banking and financial regulations
- High Availability: 99.99% uptime guarantees
- Low Latency: Sub-millisecond data access
- Disaster Recovery: Multi-site disaster recovery capabilities
Healthcare
- Data Privacy: Protect patient data and medical records
- Compliance: Meet healthcare regulatory requirements
- Integration: Integration with healthcare systems
- Backup: Automated backup and recovery
Manufacturing
- IoT Integration: Support for industrial IoT data
- Real-time Processing: Real-time data processing and analytics
- Edge Computing: Edge storage and computing capabilities
- Scalability: Scale to handle massive data volumes
Cost Optimization
Pricing Models
- Pay-as-you-go: Pay only for resources consumed
- Monthly Subscription: Reserved capacity for predictable workloads
- Yearly Subscription: Long-term commitments for better pricing
- Resource Packages: Bundled resources for cost optimization
Cost Management
- Usage Monitoring: Monitor resource usage and costs
- Budget Management: Set budgets and cost alerts
- Cost Analysis: Detailed cost analysis and recommendations
- Optimization: Automated cost optimization recommendations
Resource Optimization
- Right-sizing: Optimize instance sizes for workloads
- Auto Scaling: Scale resources based on demand
- Scheduled Scaling: Scale based on predictable patterns
- Resource Tagging: Tag resources for cost allocation
Migration Services
Cloud Migration Service
- Assessment: Assess current infrastructure and applications
- Planning: Develop comprehensive migration strategy
- Execution: Execute migration with minimal downtime
- Validation: Validate migrated systems and data
Data Replication Service (DRS)
- Real-time Replication: Real-time data replication
- Migration: Database and application migration
- Synchronization: Keep data synchronized across environments
- Monitoring: Monitor replication status and performance
Server Migration Service (SMS)
- Physical to Cloud: Migrate physical servers to cloud
- Virtual to Cloud: Migrate virtual machines to cloud
- Automated Migration: Automated migration tools
- Testing: Test migrated systems before cutover
Best Practices
Architecture Best Practices
- Multi-AZ Deployment: Deploy across multiple availability zones
- Load Balancing: Use load balancers for high availability
- Auto Scaling: Implement auto scaling for elasticity
- Backup Strategy: Implement comprehensive backup and recovery
Security Best Practices
- Least Privilege: Grant minimum required permissions
- Encryption: Enable encryption for data at rest and in transit
- Network Security: Use VPC and security groups
- Monitoring: Implement security monitoring and alerting
Performance Best Practices
- Instance Selection: Choose appropriate instance types
- Storage Optimization: Use appropriate storage types
- Network Optimization: Optimize network configuration
- Caching: Implement caching for better performance
Cost Optimization Best Practices
- Resource Planning: Plan resource requirements carefully
- Regular Reviews: Regularly review and optimize costs
- Reserved Instances: Use reserved instances for predictable workloads
- Lifecycle Policies: Implement data lifecycle policies
Support and Services
Technical Support
- 24/7 Support: Round-the-clock technical support
- Dedicated Support: Dedicated support for enterprise customers
- Expert Consultation: Access to cloud experts
- Training: Comprehensive training programs
Professional Services
- Architecture Design: Design optimal cloud architecture
- Implementation: Professional implementation services
- Migration: End-to-end migration services
- Optimization: Ongoing optimization services
Partner Ecosystem
- System Integrators: Access to certified partners
- ISV Partners: Integration with software vendors
- Training Partners: Access to training providers
- Marketplace: Huawei Cloud Marketplace solutions
Getting Started
Prerequisites
- Huawei Cloud Account: Set up account with appropriate permissions
- VPC Configuration: Configure Virtual Private Cloud
- Security Setup: Configure security groups and IAM
- Network Planning: Plan network architecture
Quick Start Guide
- Launch ECS Instances: Launch compute instances
- Configure Storage: Set up storage volumes
- Install RustFS: Install and configure software
- Network Setup: Configure networking
- Testing: Test functionality and performance
- Production: Deploy to production environment
Next Steps
- Monitoring: Set up monitoring and alerting
- Backup: Configure backup and disaster recovery
- Security: Implement security best practices
- Optimization: Optimize performance and costs
- Scaling: Plan for future growth and scaling